
Advisory on Badlock Vulnerability
This is a security advisory on the Badlock Bug.
What is Badlock?
Samba is an important component to seamlessly integrate Linux/Unix Servers and Desktops into Active Directory environments. It can function both as a domain controller and as a regular domain member. On April 12th, 2016 Badlock, a crucial security bug in Windows and Samba was disclosed. The security vulnerabilities can be mostly categorized as man-in-the-middle or denial of service attacks.
Man-in-the-middle (MITM) attacks:
There are several MITM attacks that can be performed against a variety of protocols used by Samba. These would permit execution of arbitrary Samba network calls using the context of the intercepted user. Impact examples of intercepting administrator network traffic:
- Samba AD server – view or modify secrets within an AD database, including user password hashes, or shutdown critical services.
- Standard Samba server – modify user permissions on files or directories.
Denial-of-Service (DoS) attacks:
Samba services are vulnerable to a denial of service from an attacker with remote network connectivity to the Samba service. Microsoft has addressed this in MS16-047. This vulnerability can be used to login as another user for applications that use the SAMR or LSAD protocol. All versions of Windows are affected.
Who is Vulnerable?
Samba Application running on Linux/Unix Systems
- 3.6.x,
- 4.0.x,
- 4.1.x,
- 4.2.0-4.2.9,
- 4.3.0-4.3.6,
- 4.4.0
Windows
All supported editions of Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, and Windows 10.
Associated CVEs
Badlock for Samba is referenced by CVE-2016-2118 (SAMR and LSA man in the middle attacks possible) and for Windows by CVE-2016-0128 / MS16-047 (Windows SAM and LSAD Downgrade Vulnerability).
There are additional CVEs related to Badlock. Those are:
- CVE-2015-5370 (Multiple errors in DCE-RPC code)
- CVE-2016-2110 (Man in the middle attacks possible with NTLMSSP)
- CVE-2016-2111 (NETLOGON Spoofing Vulnerability)
- CVE-2016-2112 (LDAP client and server don’t enforce integrity)
- CVE-2016-2113 (Missing TLS certificate validation)
- CVE-2016-2114 (“server signing = mandatory” not enforced)
- CVE-2016-2115 (SMB IPC traffic is not integrity protected)
You’ll see output like this:
Output:
4.4.0-42-generic #62-Ubuntu SMP Fri Oct 7 23:11:45 UTC 2016
If your version is earlier than the following, you are affected:
- 4.8.0-26.28 for Ubuntu 16.10
- 4.4.0-45.66 for Ubuntu 16.04 LTS
- 3.13.0-100.147 for Ubuntu 14.04 LTS
- 3.2.0-113.155 for Ubuntu 12.04 LTS
- 3.16.36-1+deb8u2 for Debian 8
- 3.2.82-1 for Debian 7
- 4.7.8-1 for Debian unstable
How to check if server is vulnerable?
A server is vulnerable to BADLOCK if:
- It is running any of the above mentioned versions of SAMBA
- For vulnerable Windows versions refer the following link:
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2016/ms16-047
How ControlCase CaaS Customers can request a test for Badlock Vulnerability?
ControlCase Compliance as a Service (CaaS) customers can request “Badlock Vulnerability Scan” by using following steps:
-
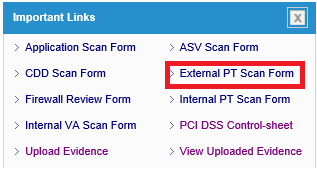
- Login to IT GRC portal
- Click “External PT Scan Form” link on the dashboard
-
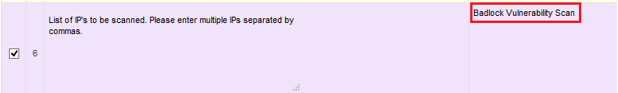
- Fill the External Network Penetration Test form with all the details and mention “Badlock Vulnerability Scan” before filling public IP addresses against #6
-
- Provide credentials to do the authenticated scan.
- Once form is filled completely, click Notify button on top right corner.
![]()
How to fix
For Samba service running on Linux/Unix systems, apply the patches provided by the Samba Team and SerNet for EnterpriseSAMBA / SAMBA+ immediately.
Patched versions are (both the interim and final security release have the patches):
- 4.2.10 / 4.2.11,
- 4.3.7 / 4.3.8,
- 4.4.1 / 4.4.2.
For Windows Installations, refer following link for patch details:
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2016/ms16-047
References and Useful Links
https://www.samba.org/samba/latest_news.html#4.4.2
https://www.samba.org/samba/security/CVE-2016-2118.html
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2016/ms16-047