
Windows OLE RCE – The Sandworm Exploit
This is a security advisory on the “Windows OLE Remote Code Execution Vulnerability” widely known as “The Sandworm” exploit.
About the Vulnerability
On October 14th, Microsoft released several Patches on the Patch Tuesday. The patches mainly address a vulnerability widely being exploited and has been named as “Sandworm”. The vulnerability allows an attacker to remotely execute arbitrary code on the user machine. This requires the victim to open a Microsoft Office file that contains specially crafted OLE object. An attacker who successfully exploited this vulnerability could assume the role of the current user on the target machine.
How ControlCase CaaS Customers can request a test for Sandstorm Vulnerability
ControlCase can perform a Sandworm scan for your infrastructure and provide you with the results. ControlCase Compliance as a Service (CaaS) customers can request “Sandworm Test” by using the following steps:
-
- Login to IT GRC portal
- Click “External PT Scan Form” link on the dashboard
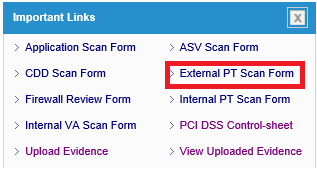
-
- Fill the External Network Penetration Test form with all the details and mention “Sandworm Test” before filling public IP addresses.
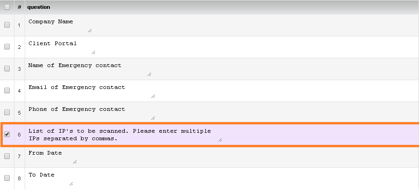
-
- Once form is filled completely, click Notify button on top right corner
![]()
How to fix
Microsoft has released a set of patches for Windows Vista, 2008, 7, 2008 R2, 8, 2012, 8.1, and 2012 R2. Performing a Windows Update will install the relevant patches automatically. his patch replaces some old patches for select Windows OS. The information related to the patches are available on Microsoft advisory link.
https://technet.microsoft.com/library/security/ms14-060
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-4114