
OpenSSL Critical Patch Update Advisory
This is a security advisory on the “OpenSSL Critical Patch Update.”
About the Vulnerability
On June 5th, the OpenSSL team published fixes for six security vulnerabilities in the widely used crypto library. OpenSSL components DTLS, do_ssl3, ssl3_read_bytes, ECDH ciphersuites are known to be having security flaws which have been fixed. According to researchers some of these issues have existed for many years in the OpenSSL but were not discovered.
The issues identified in the vulnerable OpenSSL versions allow eavesdropping on encrypted connections leading to Man-in-the-middle attacks. This can be exploited by a Man-in-the-middle (MITM) attack where the attacker can decrypt and modify traffic from the attacked client and server or can lead to denial of service.
Importantly, it affects the new versions which fixed heartbleed and all versions of OpenSSL.
How to fix
OpenSSL recommends following:
- OpenSSL 0.9.8 DTLS users should upgrade to 0.9.8za
- OpenSSL 1.0.0 DTLS users should upgrade to 1.0.0m
- OpenSSL 1.0.1 DTLS users should upgrade to 1.0.1h
How ControlCase CaaS Customers can request a test for OpenSSL
ControlCase can perform an OpenSSL vulnerability scan for your infrastructure and provide you with the results. ControlCase Compliance as a Service (CaaS) customers can request “OpenSSL Vulnerability Test” by using the following steps:
-
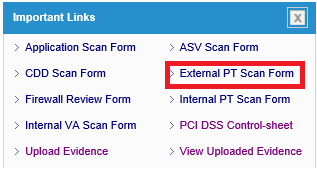
- Login to IT GRC portal
- Click “External PT Scan Form” link on the dashboard
-
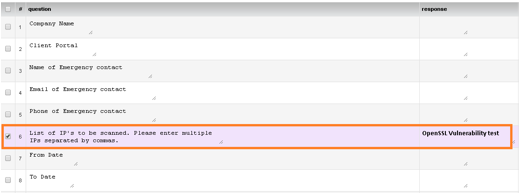
- Fill the External Network Penetration Test form with all the details and mention “OpenSSL Vulnerability test” before filling public IP addresses against #6
-
- Once form is filled completely, click Notify button on top right corner
![]()