
ControlCase Advisory on Heartbleed Security Vulnerability
This is a security advisory on the “Heartbleed” vulnerability.
What is HeartBleed Bug
The bug, called “Heartbleed”, affects servers running a package called OpenSSL. This is considered a serious vulnerability because of wide use of OpenSSL library by major applications.
The Bug was introduced to OpenSSL in December 2011 and has been out in the wild since OpenSSL release 1.0.1 on March 14, 2012.
The Bug is in the OpenSSL’s implementation of the TLS/DTLS (transport layer security protocols) heartbeat extension (RFC6520). When it is exploited it leads to the leak of memory contents from the server to the client and from the client to the server.
Heartbleed allows reading memory of systems protected by the vulnerable versions of the OpenSSL software. The bug allows an attacker to pull 64k at random from a given server’s working memory. Therefore, anyone could simply pull small bits of data from a server, over and over, until they gain the private keys needed to read all of the information that’s there.
Heartbleed and Open OpenSSL Versions
Vulnerable
OpenSSL 1.0.1 through 1.0.1F (inclusive)
Not Vulnerable
OpenSSL 1.0.1g
OpenSSL 1.0.0 branch
OpenSSL 0.9.8 branch
OpenSSL 1.0.1g released on 7th of April 2014 fixes the bug.
How ControlCase CaaS Customers can request test for Heartbleed
ControlCase can perform Heartbleed test for your infrastructure and provide you the results. ControlCase Compliance as a Service (CaaS) customers can request “Heartbleed Test” by using following steps:
-
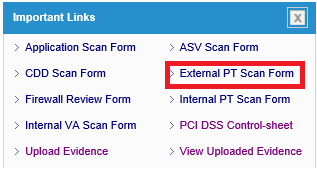
- Login to IT GRC portal
- Click “External PT Scan Form” link on the dashboard
-
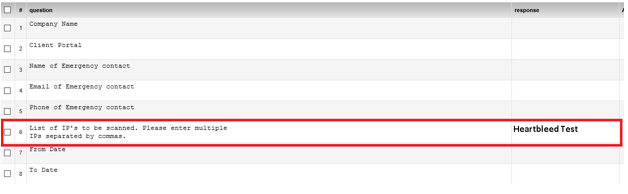
- Fill the External Network Penetration Test form with all the details and mention “Hearbleed test” before filling public IP addresses against #6
-
- Once form is filled completely, click Notify button on top right corner
![]()
How to test if you are vulnerable
Enterprises can test their infrastructure by checking the OpenSSL library version in use on your server and check if that is OpenSSL 1.0.1 through 1.0.1f. This means you are running vulnerable version of OpenSSL. You can also use following experimental free tool to check if your web server is vulnerable.
https://www.ssllabs.com/ssltest/
Individual users should try to avoid connecting to vulnerable sites and services until they notify you of a fix. Changing your password will not help till the bug is fixed by the application vendor. If a site is not vulnerable but doesn’t issue a statement, change your passwords just in case they were vulnerable in the past.
How to fix
Upgrade to fixed version 1.0.1g or newer
References
http://www.openssl.org/news/secadv_20140407.txt