CMMC Certification – ControlCase is Now an Authorized C3PAO
Your Trusted Partner for CMMC Compliance & Certification
ControlCase is officially an Authorized CMMC Third-Party Assessment Organization (C3PAO), meaning we don’t just help you prepare for CMMC certification — we now certify organizations seeking CMMC Level 2 compliance.
As a leading provider of AI-driven cybersecurity, compliance, and certification services, we bring 20+ years of expertise and an unmatched track record of securing the Defense Industrial Base (DIB).
Why Choose ControlCase for CMMC?
Authorized to Certify: As an Authorized C3PAO, we conduct official CMMC Level 2 assessments.
Fast-Track Your Compliance: Our expert team and advanced technology streamline evidence collection, automate assessments, and simplify remediation, helping you achieve certification faster and more efficiently.
End-to-End CMMC Readiness & Certification: From gap assessments to official certification, we provide full-spectrum support, ensuring zero surprises during your audit.
Deep Defense Expertise: We’ve worked with hundreds of DIB contractors, helping them meet and exceed DoD cybersecurity requirements.
What is CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a mandatory cybersecurity framework developed by the U.S. Department of Defense (DoD) to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
To win and retain DoD contracts, Defense Industrial Base (DIB) contractors must achieve and maintain CMMC compliance.
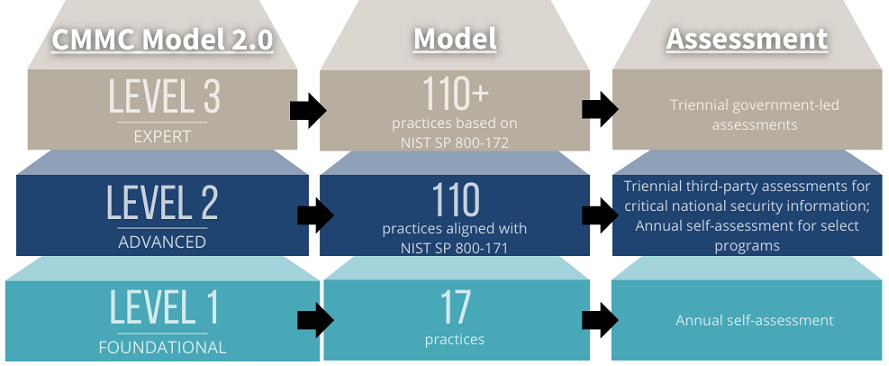
CMMC 2.0 – The Three Levels
CMMC measures cybersecurity maturity at three distinct levels:
Level 1 – Basic Cyber Hygiene: Foundational security practices to protect Federal Contract Information (FCI).
Level 2 – Advanced Cyber Hygiene: Aligns with NIST 800-171 requirements to secure Controlled Unclassified Information (CUI). (This is where C3PAO assessments come in!)
Level 3 – Expert Cybersecurity: Advanced controls for contractors handling highly sensitive DoD information.
How to Get CMMC Certified with ControlCase
Path 1: Readiness & Compliance Support (Steps 1 & 2 Only)
If you need help preparing for CMMC, we provide:
Step 1: Readiness Assessment – Identify security gaps, calculate your SPRS score, and develop a remediation plan.
Step 2: Remediation Support—aligning scope, building SSPs, mapping CUI dataflows, and validating compliance to streamline your certification success.
If we assist with readiness and remediation, we cannot perform your official CMMC certification (Step 3), but we have an incredible network of teams that can help you balance and complete your compliance journey.
Path 2: Official CMMC Certification (Step 3 Only)
Step 3: CMMC Certification Assessment – If you are already CMMC-ready and have not received readiness or remediation support from us, we can conduct your official CMMC Level 2 audit and certification as an Authorized C3PAO.
Already CMMC-ready? Let’s schedule your official assessment today.
Get Started – Secure Your DoD Contracts Today
Don’t risk non-compliance. Whether you need a CMMC readiness assessment or a certification audit, ControlCase is your partner.
