
Cross-protocol attack on TLS using SSLv2 (DROWN Vulnerability) (CVE-2016-0800)
This is a security advisory on the DROWN Attack (CVE-2016-0800).
What is DROWN Attack (CVE-2016-0800).
DROWN, stands for “Decrypting RSA with Obsolete and Weakened eNcryption”, is a serious vulnerability that affects HTTPS and other services that rely on SSL and TLS, some of the essential cryptographic protocols for Internet security. These protocols allow everyone on the Internet to browse the web, use email, shop online, and send instant messages without third-parties being able to read the communication.
Any communication between users and the server, typically includes, but is not limited to, usernames and passwords, credit card numbers, emails, instant messages, and other sensitive information. Under some common scenarios, an attacker can also impersonate a secure website and intercept or change the content the user sees.
A group of security researchers discovered that SSLv2 (Secure Sockets Layer protocol version 2.0) is vulnerable to the Bleichenbacher RSA padding oracle attack, which can be used to decrypt RSA cipher text without the knowledge of the matching private RSA key. This can be done by observing responses from a server that has the private key and performs the decryption of attacker-provided cipher texts using that key. A cross-protocol attack was discovered that could lead to decryption of TLS sessions by using a server supporting SSLv2 and export cipher suites such as Bleichenbacher RSA padding oracle. The cross-protocol attack allows decryption of SSL/TLS sessions using newer protocol versions – SSLv3 or any current TLS (Transport Layer Security) version (1.0 – 1.2) – using this SSLv2 weakness. Note that traffic between clients and non-vulnerable servers can be decrypted provided another server supporting SSLv2 and EXPORT ciphers (even with a different protocol such as SMTP, IMAP or POP) shares the RSA keys of the non-vulnerable server (CVE-2016-0800. This flaw is SSLv2 protocol issue and affects all implementations of the protocol.
Who is Vulnerable?
Websites, mail servers, and other TLS-dependent services are at risk for the DROWN attack.
How to check if server is vulnerable
A server is vulnerable to DROWN if:
- It allows SSLv2 connections. This is surprisingly common, due to misconfiguration and inappropriate default settings.
- Its private key is used on any other server that allows SSLv2 connections, even for another protocol.
How ControlCase CaaS Customers can request a scan to check this vulnerability?
ControlCase Compliance as a Service (CaaS) customers can request “DROWN Vulnerability Scan” by using following steps:
-
- Login to IT GRC portal
- Click “Internal VA Scan Form” link on the dashboard
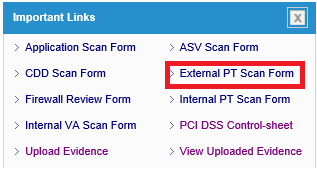
-
- Fill the External Network Penetration Test form with all the details and mention “DROWN Vulnerability Scan” before filling public IP addresses against #6
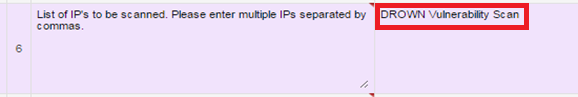
-
- Once form is filled completely, click Notify button on top right corner.
![]()
Note: We will require credentials (other than root) to detect this flaw during scan.
This scan can also be performed for Internal Systems from the ControlCase Appliance.
How to fix
It is recommend to:
- Ensure that servers private keys are not used anywhere with server software that allows SSLv2 connections. This includes web servers, SMTP servers, IMAP and POP servers, and any other software that supports SSL/TLS.
- OpenSSL 1.0.2 users should upgrade to 1.0.2g, OpenSSL 1.0.1 users should upgrade to 1.0.1s
- Disable the complete support of SSLv2 by following the vendor’s advisory:
Internet Information Services (IIS)
Apache
Postfix
Nginx
IBM HTTP Server
References and Useful Links
https://drownattack.com/
https://www.openssl.org/news/secadv/20160301.txt
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-0800
https://drownattack.com/drown-attack-paper.pdf