Many interdependencies exist between the security and privacy-related tasks demanded by compliance frameworks such as HIPAA, CCPA, and GDPR. The business implication is that enterprise security and privacy teams need to work together. Commercial platforms must also support this coordination – and the ControlCase solution is offered as a case study.
Introduction
Modern enterprise security teams must address many different types of requirements as they create their cyber defenses. These requirements can be internally generated, customer requested, legally defined, mandated by a court, or driven by an incident. They typically involve adding new protections such as cyber security platforms or increasing assurance such as through penetration testing.
Security teams must also address the best practices included in the various frameworks that have emerged during the past decade. In addition to security frameworks such as NIST Cyber Security Framework (SF), they must also deal with privacy frameworks such as the Health Insurance Portability and Accountability Act (HIPAA), California Consumer Protection Act (CCPA), and the General Data Protection Regulation (GDPR).
In this report, we review the differences between security and privacy frameworks, and how they are used by security and privacy teams. Data loss is shown to be vulnerable to several attack cases, and that both security and privacy teams are required to work together to prevent all bad outcomes. Specifically, without attention to both security and privacy concerns, it is unlikely that any complex organization will be able to ensure proper control of data.
Security Frameworks
To begin – let’s recognize that sensitive data can be leaked in three different ways: It can be leaked accidentally, such as an email sent unintentionally to the wrong recipient; it can be leaked intentionally, such as by a compromised insider; or it can be leaked as a result of bad policy, where the data is shared inappropriately as part of some business practice. Security frameworks address the first of these two cases.
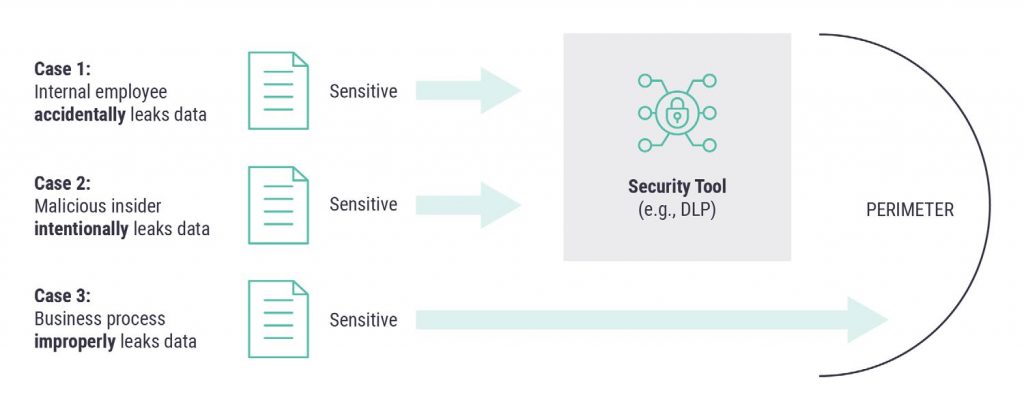 Figure 1. Security Coverage of Data Leakage
Figure 1. Security Coverage of Data Leakage
The two main cases in which data is accidentally leaked by an insider and data is intentionally leaked or stolen by a malicious actor are specifically addressed by security teams. The typical types of controls used include data leakage prevention (DLP) systems, user behavior analytics (UBA) tools, and various types of encryption. These tools work reasonably well, but security teams continue to try to improve their coverage and accuracy.
It is especially interesting to see, however, that security teams cannot and do not address the use case where businesses improperly leak data due to weak or poorly conceived business practices. That is, if product or service teams decide that it’s perfectly fine to sell customer data to a third party (a fact often hidden in the fine print of terms and conditions documents), then this is technically not a security issue. Customer might not like it – but this is not a breach.
Privacy Frameworks, Policies, and Platforms
Privacy frameworks have thus been developed to help define an organization’s intentional business practices regarding data handling. They complement security systems by helping an organization make good decisions about how to empower customers to take control of their data, and to support the rights and privileges of data owners. These decisions must take into account customer preferences, local laws, and technological feasibility.
In the best case, the implementation of security and privacy controls – driven by their respective frameworks – will be set up to coordinate and cooperate functionally. Both security and privacy control systems should, for example, generate audit log evidence of effectiveness so that auditors or assessors can gain confidence that things are working properly. Figure 2 shows how these controls might complete the data protection picture.
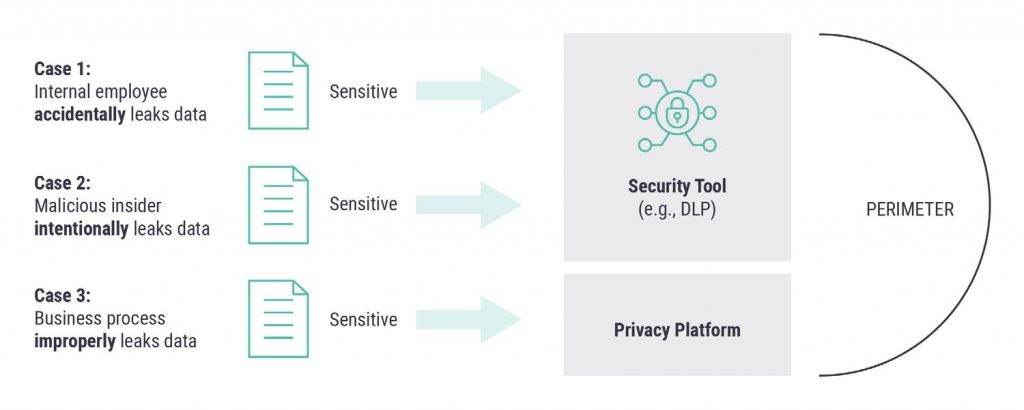 Figure 2. Privacy Coverage of Data Leakage
Figure 2. Privacy Coverage of Data Leakage
The most popular and often-cited privacy frameworks are the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the California Consumer Privacy Act (CCPA). While many differences apply, all three frameworks are intended to protect the rights of users to control and manage their data. Unlike security frameworks, however, they focus on business practices rather than stopping hackers.
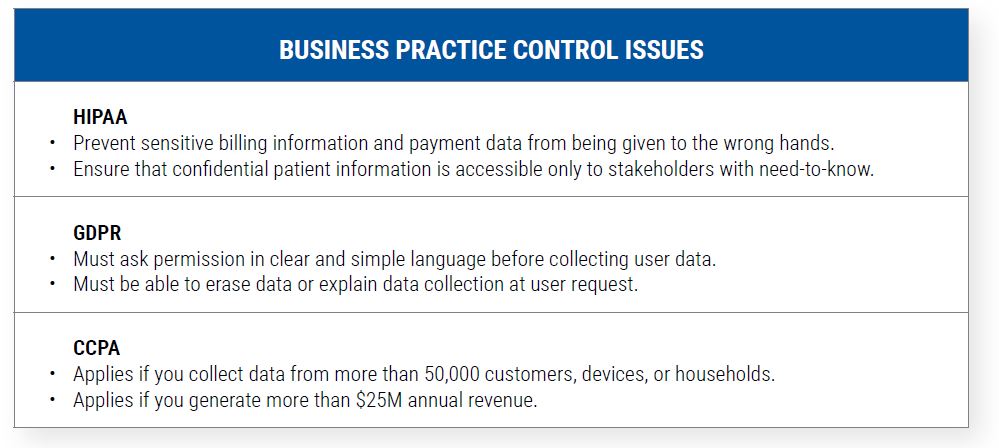 Figure 3. Comparing GDPR, HIPAA, and CCPA
Figure 3. Comparing GDPR, HIPAA, and CCPA
The key issue here is that business practices can only control the management of data if the underlying mechanisms are in fact secure. If there are hacked data leaks to patient data, for example, then any business pledge to satisfy HIPAA cannot be made. In the next section, we outline this important interdependency, and we provide a roadmap for enterprise security and privacy teams to coordinate on a common set of objectives.
Coordination Between Security and Privacy
To learn more about the Coordination between Security and Privacy, and to receive our free 3-Step action plan for Enterprise, please download our whitepaper.
About TAG Cyber
TAG Cyber is a trusted cyber security research analyst firm, providing unbiased industry insights and recommendations to security solution providers and Fortune 100 enterprises. Founded in 2016 by Dr. Edward Amoroso, former SVP/CSO of AT&T, the company bucks the trend of pay-for-play research by offering in-depth research, market analysis, consulting, and personalized content based on hundreds of engagements with clients and non-clients alike—all from a former practitioner perspective.
Copyright © 2021 TAG Cyber LLC. This report may not be reproduced, distributed, or shared without TAG Cyber’s written permission. The material in this report is comprised of the opinions of the TAG Cyber analysts and is not to be interpreted as consisting of factual assertions. All warranties regarding the correctness, usefulness, accuracy, or completeness of this report are disclaimed herein.
Prepared by Dr. Edward G. Amoroso
Chief Executive Officer, TAG Cyber LLC
Research Professor NYU Center for Cyber Security (CCS)
eamoroso@tag-cyber.com
