Perhaps you’re learning about HITRUST and wondering ‘what is HITRUST certification’? Or, ‘what does HITRUST stand for’? This blog offers everything you need to know about the HITRUST framework, HITRUST certification requirements, and the 2023 updates.
HITRUST
HITRUST, created by the HITRUST Alliance, is a leading certification in the industry.
- Founded in 2007 to help companies safeguard sensitive data and manage risk.
- Established a certifiable framework for organizations that create, access, store, or exchange covered or sensitive information.
- Originated from the belief that information security is critical to the widespread utilization of and confidence in health information systems, medical technologies, and electronic exchanges of medical data. Now, the HITRUST CSF is industry agnostic.
WHAT IS HITRUST CSF
The HITRUST CSF rationalizes and harmonizes relevant data protection regulations and standards into a single overarching security and privacy framework. The HITRUST CSF provides an overall methodology that enables organizations to effectively evaluate compliance and security risk.
The HITRUST CSF:
- Provides organizations the ability to tailor their security control baselines when obtaining a certification to what is applicable based on their specific information security requirements.
- Incorporates both compliance and risk management principles.
- Defines a process to evaluate compliance and security risk effectively and efficiently.
- Is the framework used for HITRUST Certification.
Key Components of the CSF Assurance Program
There are 3 high-level components associated with the HITRUST CSF: Questionnaires, External Assessors (such as Control Case), and Reports.
| Questionnaires | External Assessors/Auditors (such as ControlCase) | Reports |
|---|---|---|
| Controls applicable to your organization that are used to measure risk and compliance. | Uses the questionnaire to assess adherence to the HITRUST CSF. | The deliverable that can show stakeholders and customers that your organization is HITUST Certified. |
2023 UPDATES TO HITRUST
HITRUST recently announced a new version of the CSF called version 11, replacing version 9.6.2.
Summary of Changes in HITRUST v11
- Added selectable compliance factors and refreshed various mappings to authoritative sources.
- Moved evaluative elements from the Policy Illustrative Procedure to the Requirement Statement.
- Updated Illustrative Procedure Content.
- Performed assorted errata updates consistent with the CSF Versioning Policy.
New Certification: e1 Assessment
- Basic cybersecurity hygiene.
- Less than 50 requirement statements.
- Annual certification.
- Quicker assurance.
TYPES OF HITRUST ASSESSMENTS
Complete portfolio of the types of HITRUST assessments and certifications:

There are 5 maturity levels within the CSF when it comes to testing: policy, procedure, implemented, measured, and managed.
A readiness assessment is typically not a certification. It’s a self-assessment that organizations can do to identify gaps in their environment. While not required for a HITRUST readiness assessment, an external assessor, like ControlCase, can absolutely be utilized to gain expert assistance and opinion.
A validated assessment allows organizations to submit the assessment for HITRUST certification. It requires an external assessor, like ControlCase, to prepare the entities for and perform the audit.
For v11, the HITRUST framework has aligned the selection of requirement statements used for the e1 assessment, i1 assessment, and r2 assessment baseline so that each assessment builds upon the core requirement statements that are included in the e1 assessment. The following chart shows how the assessments flow together (based on the needs of your organization):
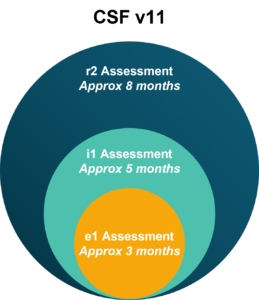
HITRUST Domains
Industry-standard categorized domains entail all requirement statements and security. These domains are reviewed to see if an organization meets the security threshold:
- Information Protection Program
- Configuration Management
- Access Control
- Business Continuity & Disaster Recovery
- Endpoint Protection
- Vulnerability Management
- Audit Logging & Monitoring
- Risk Management
- Portable Media Security
- Network Protection
- Education, Training, and Awareness
- Physical & Environmental Security
- Mobile Device Security
- Transmission Protection
- Third Party Assurance
- Data Protection & Privacy
- Wireless Security
- Password Management
- Incident Management
CONTROLCASE METHODOLOGY
ControlCase has been performing HITRUST assessments since 2014. We’ve helped over 100 customers become HITRUST certified. Through simplified timelines, an automated approach, and the help of an expert dedicated to you through every step of the way, ControlCase offers a smooth and speedy process for HITRUST certification.
ControlCase utilizes a unique 6-phase approach that places the focus on certification from the very beginning:

