The ISO 27001 Information Security Management System (ISMS) is the single most effective means of exercising managerial control over information in your organization.
ISO 27001:2022 is the latest version of the internationally recognized information security management standard, which was published on October 25, 2022. This latest version reflects the state of cyber security today, with a view to improving and managing your organization’s resilience to cyber threats. All organizations must transition to the new ISO 27001:2022 standard no later than October 31, 2025, regardless of the original registration date. All remaining ISO 27001:2013 certificates will be withdrawn and considered to be expired as of October 25, 2023, regardless of the original certification date.
In this blog, we will provide everything you need to know about the newest improvements you’ll see in ISO 27001:2022, including:
- Key changes
- What it means if your business is already certified to ISO 27001:2013.
- What to do if you’ve already started your ISO 27001 implementation.
What are the key changes in ISO 27001:2022 compared to the previous version?
The key changes in ISO 27001:2022 compared to the previous version are mainly in “Annex A” , while the changes in the main part of the standard are small to moderate. Key changes to ISO 27001 are as follows:
- Change in the title of the standard
- Minor change to clauses 4 to 10
- 11 new controls have been added to “Annex A”
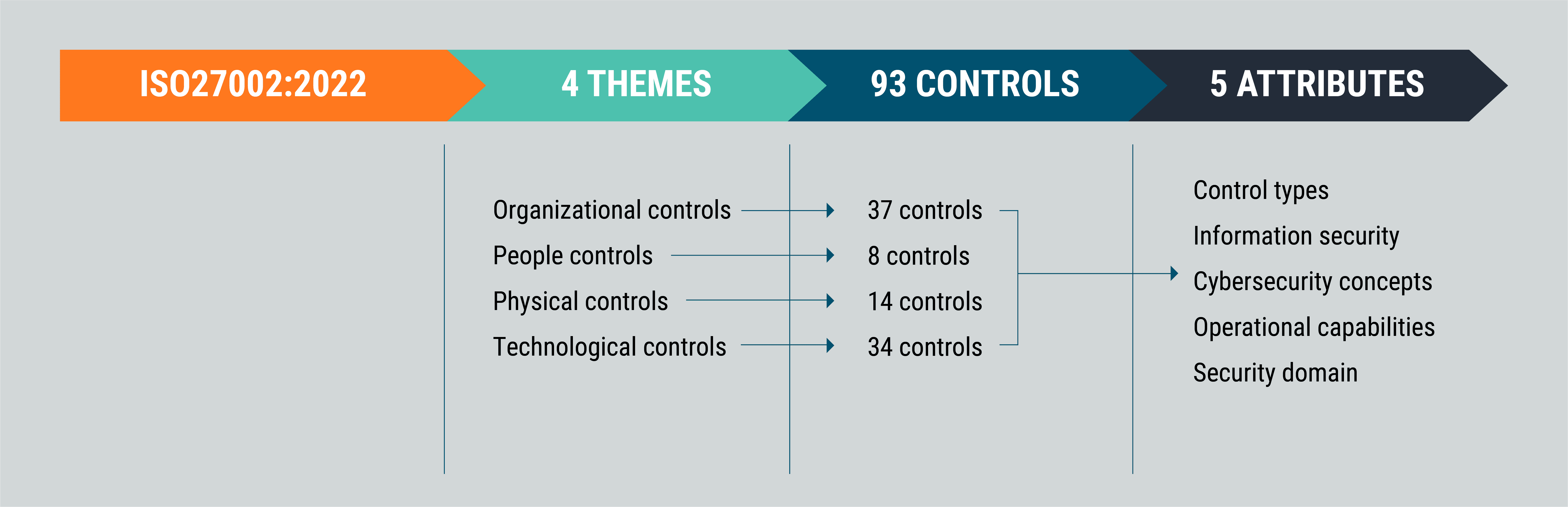
- Decreased number “Annex A” controls from 114 to 93
- “Annex A” controls are grouped into 4 sections, instead of the previous 14
Change in the title of the standard
Differing from ISO/IEC 27001:2013, the ISO 27001:2022 standard has a new title: “ISO/IEC 27001:2022 Information Security, Cyber Security and Privacy Protection”. This establishes ISO 27001:2022 as being primarily focused on cyber security, cloud services, threat intelligence, and the adoption of data protection.
Changes to the Clauses
Clauses 4 to 10 have undergone several minor changes, especially in clauses 4.2, 6.2, 6.3, and 8.1, where new content has been added. Other updates include minor changes in the terminology and restructuring of sentences and clauses. The title and order of these clauses, however, remain the same:
- Clause 4.2 – Understanding the needs and expectations of interested parties
- Clause 5.3 – Organizational roles, responsibilities and authorities
- Clause 6.1.3 – Information security risk treatment
- Clause 6.2 – Information security objectives and planning to achieve them
- Clause 6.3 – Planning of changes
- Clause 7.4 – Communication
- Clause 8.1 – Operational planning and control
- Clause 9.3 – Management review
Changes to the Annexure A
“Annex A” of ISO/IEC 27001:2022 contains changes in both the number of controls and their listing in groups. The title of this Annex has also changed from Reference control objectives and controls to Information security controls reference.
11 new controls were added to “Annex A”, yet the total number of controls decreased from 114 to 93. This was achieved via the following:
- 57 controls were merged into 24
- One control was separated into two
- 35 controls remained unchanged
- 23 controls were simply renamed
- 11 new controls were added
When seeking certification for information security, it is important to note that not all controls are mandatory. Companies may exclude a control if there are no related risks identified, or if there are no legal or regulatory requirements to implement a particular control.
The 11 new controls come by way of recognizing advancements in technology and the risk landscape since the 2013 release. Specifically, these controls are as follows:
- Threat intelligence (5.7): requires companies to collect and analyze information relating to information security threats
- Information security for use of cloud services (5.23): requires companies to specify and manage information security for the use of cloud services
- ICT readiness for business continuity (5.30): requires companies to create an ICT continuity plan to maintain operational resilience
- Physical security monitoring (7.4): requires companies to detect and prevent external and internal intruders by deploying suitable surveillance tools
- Configuration management (8.9): requires companies to establish policies to manage how they document, implement, monitor, and review the use of configurations across their entire network
- Information deletion (8.10): provides guidance on how to manage data deletion to comply with laws and regulations
- Data masking (8.11): provides data masking techniques for personal identifiable information (PII) to comply with laws and regulations
- Data leakage protection (8.12): requires companies to implement technical measures that detect and prevent the disclosure and/or extraction of information
- Monitoring activities (8.16): provides guidance on improving network monitoring activities to identify anomalous behavior and address security events and incidents
- Web filtering (8.23): requires companies to enforce access controls and measures to restrict and control access to external websites
- Secure coding (8.28): requires companies to follow secure coding principles to prevent vulnerabilities caused by poor coding methods
The number of controls has reduced from 114 to 93. They are now split into four themed categories, instead of the previous 14. They are:
- Section 5: People (8 controls)
- Section 6: Organizational (37 controls)
- Section 7: Physical (14 controls)
- Section 8: Technological (34 controls)
Control attributes are a new addition to the standard introduced in ISO 27001:2022. These five attributes are intended to help easily classify and group the controls based on what makes sense to their organization and security needs. ISO 27002:2022 (which provides guidance for how to implement controls outlined in ISO 27001) states in section 4.2 Themes and Attributes:
The five attributes are:
- Control type: preventative, detective, corrective
- Operational capabilities: governance, asset management, information protection, human resource security, etc.
- Security domains: governance and ecosystem, protection, defence, resilience
- Cybersecurity concepts: identify, protect, detect, respond, recover
- Information security properties: confidentiality, integrity, availability
What is the timeline for transitioning to ISO 27001:2022?
The timeline for transitioning to ISO 27001:2022 is as follows:
- The transition period began on October 31, 2022.
- Certification bodies have until October 2023 to complete their transition to the ISO 27001:2022 audit format.
- Organizations that are currently ISO 27001 certified have a three-year (36-month) transition period, which began once ISO/IEC 27001:2022 was published.
- All organizations that wish to remain certified to ISO 27001 will need to transition to the 2022 revision of the standard within the set transition period, which ends in October 2025.
- It is recommended for currently certified companies to certify for the update before the end of 2025.
To ensure a smooth transition, organizations should:
- Get a copy of the ISO 27001:2022 document to understand the new requirements.
- Review and identify changes to controls, policies, procedures, and systems that will be required to comply with the updated version of ISO 27001.
- Develop and execute a plan for making the necessary changes to align the organization with the updated requirements.
Overall, organizations have a three-year transition period to move from ISO 27001:2013 to ISO 27001:2022, with the deadline for transition being October 31, 2025.
What are the consequences of not transitioning to ISO 27001:2022 before the deadline?
The consequences of not transitioning to ISO 27001:2022 before the deadline can vary depending on the specific circumstances and requirements of each organization. However, here are some potential consequences that organizations may face:
- Non-compliance with regulatory requirements: ISO 27001 certification is often a requirement for organizations operating in certain industries or jurisdictions. Failure to transition to the updated standard may result in non-compliance with regulatory requirements, which could lead to legal and financial consequences.
- Loss of certification: Organizations that fail to transition to ISO 27001:2022 within the set transition period may lose their certification to the ISO 27001 standard. This means that they will no longer be recognized as having a compliant information security management system.
- Loss of customer trust: ISO 27001 certification is often seen as a mark of trust and credibility in the marketplace. Failure to transition to the updated standard may erode customer trust and confidence in an organization’s ability to protect their sensitive information.
- Increased security risks: The updated ISO 27001:2022 standard includes new controls and requirements that address advancements in technology and the evolving threat landscape. By not transitioning, organizations may be missing out on important security measures and leaving themselves vulnerable to potential security breaches.
- Missed business opportunities: Many organizations require their suppliers and partners to have ISO 27001 certification as a condition of doing business. Failure to transition to the updated standard may result in missed business opportunities and potential loss of contracts or partnerships.
It is important for organizations to prioritize the transition to ISO 27001:2022 to ensure ongoing compliance, maintain a strong security posture, and meet the expectations of customers and stakeholders. Organizations should plan and allocate resources accordingly to complete the transition within the set transition period, which ends in October 2025.
What are the benefits of transitioning to ISO 27001:2022?
Transitioning to ISO 27001:2022 can bring several benefits to organizations. Here are some of the key benefits of ISO 27001:2022:
- Enhanced cybersecurity practices: ISO 27001:2022 is more up-to-date with current cybersecurity practices and threats. By transitioning, organizations can align their information security management system (ISMS) with the latest industry best practices, ensuring that their security measures are robust and effective.
- Stronger assurance to stakeholders: The updated standard helps with risk management and can offer stronger assurance to stakeholders. By transitioning, organizations can demonstrate their commitment to protecting sensitive information and maintaining a secure environment, which can enhance trust and confidence among stakeholders.
- Competitive differentiation: Transitioning to ISO 27001:2022 can be a competitive differentiator for organizations. The updated release aligns with current cybersecurity practices, making the organization’s ISMS more robust. This can be perceived as a stronger attestation of security compared to certification to an older standard.
- Compliance with related standards: ISO 27001:2022 is expected to impact related standards. By transitioning, organizations can ensure that their management system aligns with the updated ISO 27001 standard and related standards, avoiding potential conflicts or inconsistencies.
- Improved data privacy protection: Implementing ISO 27001:2022 can strengthen and protect the data privacy stored by organizations. The updated standard includes measures to address data privacy concerns, helping organizations meet regulatory requirements and protect sensitive information.
- Business opportunities: ISO 27001 certification is often a requirement for organizations to do business with certain partners or in specific industries. Transitioning to ISO 27001:2022 ensures that organizations remain compliant and eligible for business opportunities that require ISO 27001 certification.
It is important for organizations to consider these benefits and prioritize the transition to ISO 27001:2022 to stay up-to-date with industry standards, enhance their security posture, and gain a competitive edge in the market.