Assess once, comply to many.
Almost every business has to comply with multiple information security related standards and regulations. IT compliance audits are complicated, expensive, and full of challenges. These can include but are not limited to PCI DSS, ISO 27001, GDPR, HIPAA, HITRUST, FISMA, NIST 800-53, MARS-E, BITS FISAP. Managing these audits individually poses a number of challenges for a business; including repetition of efforts, managing multiple audit firms, increased costs, complexity and time.
Reduce Audit Fatigue
Reduce Compliance Costs
Deal With Fewer Auditors
Reduce Audit Preparation & Execution Time
THE CONTROLCASE ONE AUDIT™ SOLUTION ENABLES ORGANIZATIONS TO PERFORM
A SINGLE AUDIT AND COMPLY TO
MULTIPLE REGULATIONS.
ONE AUDIT™ blends enterprise software solutions, hosted solutions, and managed services to streamline the creation, mapping and updating of internal and external controls, thus empowering IT, Security, and Compliance Managers to COLLECT EVIDENCE AND RISK CONTROLS ONCE AND MAP ACROSS MULTIPLE REGULATIONS. It also combines the power of our proprietary and concise questionnaire which maps multiple IT standards, regulations along with automated techniques to answer the questionnaire for different IT infrastructures by one Audit Firm with the outcome of multiple certifications.
One Audit Consolidated Regulations & Standards
PCI DSS
ISO 27001 & 27002
GDPR
HIPAA
NIST 800-53
FISMA
SOC2
SCA
One Audit Timeline & Approach
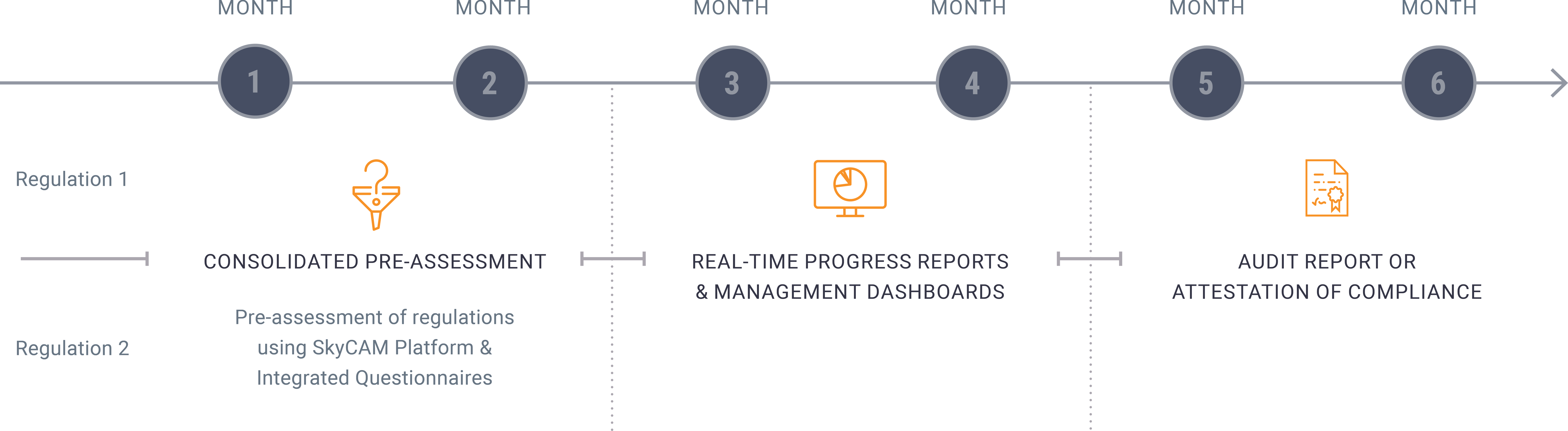
THE ONE AUDIT SOLUTION INCLUDES:
- Dashboards with flexible reporting that consolidates views of compliance efforts
- Graphical views of compliance progress across multiple regulations
- Automated evidence collection in the cloud
- Partnership approach
- Service can be delivered remotely
| Sample Mapping Question # / Question | PCI DSS | ISO 27001 | SCA | SOC2 | HIPAA | NIST 800-53 | |
| Question Number | Question | PCI DSS | ISO 27001 | SCA | SOC2 | HIPAA | NIST 800-53 |
|---|---|---|---|---|---|---|---|
| 50 | For all assets identified in the sample selected by the assessor, provide evidence of logical access account and password features including: – Account lockout policy – Account lockout duration – Session timeout policy – Password length – Password complexity – Password history – Password expiry |
8.1.6 8.1.7 8.1.8 8.2.3 8.2.4 8.2.5 |
9.3.1 9.4.2 9.4.3 |
H.5 | CC6.1 | 164.308(a)(5)(ii)(d) | AC-7 AC-11 AC-12 IA-4 IA-5 |
| 64 | Provide PCI scope Application, server, network devices and database user access (permission) list with business justification for each user – (No need to include the consumer user list for applications)
Also provide supporting system screenshot showing the current added users Security Posture QA:
|
7.1.1 | 9.2.1 9.4.1 |
D.8 | S3.2, S3.4 C3.8, PI3.2 PI3.5, P8.2.2 |
164.308(a)(3) 164.308(a)(4) 164.312(a)(1) 164.312(a)(2)(i) 164.312(d) |
AC-1 AC-2 AC-3 AC-14 |
