
SSL V3.0 Fallback – POODLE Advisory
This is a security advisory on the “SSL V3.0 Fallback – POODLE.”
About the Vulnerability
On October 14th, an attack affecting the SSLv3.0 protocol was disclosed. The attack named POODLE which is acronym for “Padding Oracle On Downgraded Legacy Encryption” allows an attacker with ability to sniff the traffic to rapidly decrypt any communication that uses SSLv3.0 or can be downgraded to SSLv3.0. Any OS, server, client, web application or service that uses communication encryption with SSLv3.0 is vulnerable to this attack vector given that the attacker has ability to sniff the communication at either end.
This attack targets the logic of padding bytes used by SSLv3.0 protocol in order to obtain plaintext from the ciphertext. As most browsers and web servers support falling back to earlier protocol version (known as “downgrade dance”) in case of failed initial SSL handshake. This behavior allows an attacker to target the client/servers that support TLSv1.0 or higher by forcing a downgrade to SSL 3.0.
How ControlCase CaaS Customers can request a test for Poodle Attack
ControlCase can perform a POODLE attack scan for your infrastructure and provide you with the results. ControlCase Compliance as a Service (CaaS) customers can request “POODLE Attack Test” by using the following steps:
-
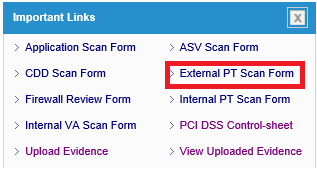
- Login to IT GRC portal
- Click “External PT Scan Form” link on the dashboard
-
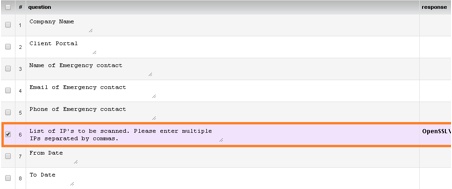
- Fill the External Network Penetration Test form with all the details and mention “POODLE Attack Test” before filling public IP addresses against #
-
- Once form is filled completely, click Notify button on top right corner
![]()
How to fix
Following are general recommendations to prevent the attack:
- Completely disabling the support for SSLv3.0 or lower
- Disabling CBC mode ciphers with SSLv3.0
Support TLS_FALLBACK_SCSV protocol to avoid downgrade attacks
References
http://googleonlinesecurity.blogspot.nl/2014/10/this-poodle-bites-exploiting-ssl-30.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
https://tools.ietf.org/html/draft-ietf-tls-downgrade-scsv-00