With the release of PCI 4.0, the countdown has started for organizations already PCI DSS Certified to transition from PCI DSS v3.2.1 to the new PCI DSS v4.0 standard. With the timelines of one year to prepare for v4.0 and two years to fully ready for v4.0 future dated requirements, it is time to assess readiness for PCI DSS v4.0 and establish a detailed plan to meet the requirements and timelines.
PCI DSS v4.0: 2022
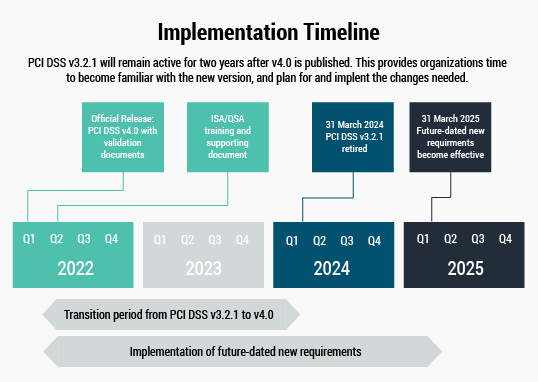
PCI Data Security Standard (PCI DSS), a global payment data standard, has been designed to provide baseline technical and operational requirements to protect payment data. PCI DSS v4.0 is the next evolution of the standard and is applicable to all entities that store, process, and/or transmit payment data elements, such as credit/debit/payment cards. Below are the timelines for migration to the latest PCI-DSS v4.0 standard:
WHY DO YOU NEED TO START PREPARING FOR PCI DSS v4.0 NOW?
PCI DSS 4.0 is already released and can be used as a version for PCI DSS Certification. Although PCI DSS 3.2.1 can be used for assessments until 31st March 2024, there are some requirements that must currently be in place to ensure the organization can be certified to PCI DSS v4.0 from 1st April 2024 onwards.
Following are the actual requirements, out of 64 total new requirements, and their effective implementation date required for all entities and service providers:
Immediately for All v4.0 Assessments
All Entities
Applicable Requirements Are:
- 2.1.2
- 3.1.2
- 4.1.2
- 5.1.2
- 6.1.2
- 7.1.2
- 8.1.2
- 9.1.2
- 10.1.2
- 11.1.2
- 12.3.2
- 12.5.2
Service Providers Only
Applicable Requirements Are:
- 2.1.2
- 3.1.2
- 4.1.2
- 5.1.2
- 6.1.2
- 7.1.2
- 8.1.2
- 9.1.2
- 10.1.2
- 11.1.2
- 12.3.2
- 12.5.2
- 12.9.2
Effective 31 March 2025
All Entities
Applicable Requirements Are:
- 3.2.1
- 3.3.2
- 3.4.2
- 3.5.1.1
- 3.5.1.2
- 4.2.1
- 4.2.1.1
- 5.2.3.1
- 5.3.2.1
- 5.3.3
- 5.4.1
- 6.3.2
- 6.4.2
- 6.4.3
- 7.2.4
- 7.2.5
- 7.2.5.1
- 8.3.6
- 8.4.2
- 8.5.1
- 8.6.1
- 8.6.2
- 8.6.3
- 9.5.1.2.1
- 10.4.1.1
- 10.4.2.1
- 10.7.2
- 10.7.3
- 11.3.1.1
- 11.3.1.2
- 11.6.1
- 12.3.1
- 12.3.3
- 12.3.4
- 12.6.2
- 12.6.3.1
- 12.6.3.2
- 12.10.4.1
Service Providers Only
Applicable Requirements Are:
- 3.2.1
- 3.3.2
- 3.3.3
- 3.4.2
- 3.5.1.1
- 3.5.1.2
- 3.6.1.1
- 4.2.1
- 4.2.1.1
- 5.2.3.1
- 5.3.2.1
- 5.3.3
- 5.4.1
- 6.3.2
- 6.4.2
- 6.4.3
- 7.2.4
- 7.2.5
- 7.2.5.1
- 8.3.6
- 8.3.10.1
- 8.4.2
- 8.5.1
- 8.6.1
- 8.6.2
- 8.6.3
- 9.5.1.2.1
- 10.4.1.1
- 10.4.2.1
- 10.7.2
- 10.7.3
- 11.3.1.1
- 11.3.1.2
- 11.4.7
- 11.5.1.1
- 11.6.1
- 12.3.1
- 12.3.3
HOW TO TRANSITION TO PCI DSS v4.0 WITHIN A TIMELINE
The transition period is meant to allow organizations time to get familiar with the changes present in PCI DSS 4.0 while completing necessary updates to policy/procedure templates, planning for organizational changes, and implementing additional controls that will allow them to meet the modernized requirements.
The efforts for transition can be divided into two parts:
- Address controls related to immediately effective requirements:
- These controls are largely related to documenting roles and responsibilities.
- Perform targeted risk analysis for each PCI DSS requirement that is met with the customized approach.
- Document and confirm PCI DSS scope at least once every 12 months.
- TPSPs support customers’ requests to provide PCI DSS compliance status and information about PCI DSS requirements that are the responsibility of the TPSP. This is an additional requirement for service providers only.
- Start Implementing the following controls, which are best practice until 31 March 2025:
- Storage of sensitive authentication data (SAD) should be minimized, and it should be stored encrypted using strong cryptography prior to completion of authorization. This applies to issuers too.
- Technical controls to prevent copy and/or relocation of PAN when using remote-access technologies, except with explicit authorization.
- Securing PAN by hashing should use keyed cryptographic hashes of the entire PAN with associated key-management.
- Implementation of disk-level or partition-level encryption when used to render PAN unreadable.
- Certificates used to safeguard PAN during transmission over open, public networks are confirmed as valid and are not expired or revoked.
- A targeted risk analysis is performed to determine frequency of:
- Periodic evaluations of system components identified as not at risk for malware.
- Periodic malware scans.
- Anti-malware scans are performed when removable electronic media is in use.
- Mechanisms are in place to detect and protect personnel against phishing attacks.
- Maintain an inventory of bespoke and custom software to facilitate vulnerability and patch management.
- Deploy an automated technical solution for public-facing web applications that continually detects and prevents web-based attacks.
- Manage all payment page scripts that are loaded and executed in the consumer’s browser.
- Review all user accounts and related access privileges appropriately.
- Assign and manage all application and system accounts and related access privileges appropriately.
- Minimum level of complexity for passwords when used as an authentication factor.
- If passwords/passphrases are the only authentication factor for customer user access, passwords/passphrases are changed at least every 90 days, or the security posture of accounts is dynamically analyzed to determine real-time access to resources.
- Multi-factor authentication for all access into the CDE.
- Passwords/passphrases used for interactive login for application and system accounts are protected against misuse.
- A targeted risk analysis is performed to determine frequency of periodic POI device inspections.
- Audit log reviews are automated.
- A targeted risk analysis is performed to determine frequency of log reviews for all other system components.
- Failures of critical security control systems are detected, alerted, and addressed promptly.
- Internal vulnerability scans are performed via authenticated scanning.
- Multi-tenant service providers support their customers for external penetration testing.
- Covert malware communication channels detect, alert, and/or prevent, and address via intrusion-detection and/or intrusion-prevention techniques.
- A change-and-tamper-detection mechanism is deployed for payment pages.
- A targeted risk analysis is documented to support each PCI DSS requirement that provides flexibility for how frequently it is performed.
- PCI DSS scope is documented and confirmed at least once every six months and upon significant changes.
- The impact of significant organizational changes on PCI DSS scope is documented and reviewed. Results are communicated to executive management.
- The security awareness program is reviewed at least once every 12 months and updated as needed.
- Security awareness training includes awareness of threats that could impact the security of the CDE including phishing, related attacks, and social engineering.
- Security awareness training includes awareness about acceptable use of end-user technologies.
- A targeted risk analysis is performed to determine frequency of periodic training for incident response personnel.
- The security incident response plan includes alerts from the change-and-tamper-detection mechanism for payment pages.
- Incident response procedures are in place and initiated upon detection of PAN.
- The multi-tenant service provider that confirms access to and from customer environment is logically separated to prevent unauthorized access.
- The multi-tenant service provider confirms effectiveness of logical separation controls used to separate customer environments at least once every six months via penetration testing.
- The multi-tenant service provider implements processes or mechanisms for reporting and addressing suspected or confirmed security incidents and vulnerabilities.
START THE TRANSITION WITH A PCI READINESS ASSESSMENT
Organizations getting first-time assessed for PCI DSS and those already assessed can take advantage of this service from ControlCase using the following options:
With a PCI DSS Assessment, you can minimize risks, identify security vulnerabilities, and further protect cardholder data from breaches.
When you’re ready to start implementing PCI DSS 4.0, we can help. For more information, please contact Mark Cline mcline@controlcase.com
